Difference between revisions of "Risks"
| Line 33: | Line 33: | ||
''Risks'' records are organized in four sections: | ''Risks'' records are organized in four sections: | ||
| − | * <u>''Identification''</u>, where identification data of the '' | + | * <u>''Identification''</u>, where identification data of the ''risk'' are recorded, |
| − | * <u>''Ownership & Organization''</u>, containing the assignment of the key roles enabled to manage the '' | + | * <u>''Ownership & Organization''</u>, containing the assignment of the key roles enabled to manage the ''risk''; |
| − | * <u>''Pre-mitigation Assessment''</u>, with the details of the '' | + | * <u>''Pre-mitigation Assessment''</u>, with the assessment details of the ''risk'' before mitigation actions; |
| − | * <u>''Post-mitigation Assessment''</u>, with the details of the '' | + | * <u>''Post-mitigation Assessment''</u>, with the details of the ''risk'' after mitigation actions. |
Detailed information on the meaning and use of every field can be found by pointing the mouse on the (i) next to each field. This will activate a tooltip with a brief description of the field. | Detailed information on the meaning and use of every field can be found by pointing the mouse on the (i) next to each field. This will activate a tooltip with a brief description of the field. | ||
| Line 43: | Line 43: | ||
== Privileges == | == Privileges == | ||
| − | '' | + | ''Risks'' can be created by the ''users'' to whom the corresponding privilege is granted (see [[Users & Groups]] for more information on how to set this privilege). |
| − | The lifecycle of the '' | + | The lifecycle of the ''risk'' is managed by the roles described in the table below. ''Groups'' are pre assigned to the roles according to the ''settings'' (see [[Settings]] for more information on how to set these defaults). Initial assignments can be modified according to privileges choosing among the enabled ''groups'' (see once again [[Settings]] for more information on how to enable ''groups''). |
{| class="wikitable" | {| class="wikitable" | ||
| Line 59: | Line 59: | ||
|<u>Data Processor Group</u> || Members of the ''group'' assigned to this role have view (read) privileges. | |<u>Data Processor Group</u> || Members of the ''group'' assigned to this role have view (read) privileges. | ||
|- | |- | ||
| − | |<u> | + | |<u>Risk Assessment Team</u> || Members of this ''group'' have several privileges. They can manage the entire lifecycle, being enabled to: |
* transition records to any compatible status, | * transition records to any compatible status, | ||
* update fields when possible. | * update fields when possible. | ||
| Line 69: | Line 69: | ||
* update fields when possible. | * update fields when possible. | ||
|} | |} | ||
| − | |||
| − | |||
| − | |||
== Reports == | == Reports == | ||
| − | The list of '' | + | The list of ''risks'' can be filtered and exported to excel format from the ''view'' '''''Risks'''''. |
== Related processes == | == Related processes == | ||
| − | '' | + | ''Risks'' can be related to ''actions'', ''audits'', ''data breaches'', ''issues / non conformities'', ''privacy impact assessments'' and ''processing activities''. |
Revision as of 21:17, 14 September 2018
Contents
Introduction to Risks
This workflow provides the mean to manage the lifecycle of risks related to personal data management.
Workflow
A new risk can be created using the Add New functionality and choosing "New Risk".
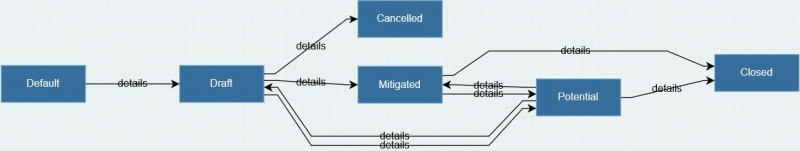
The workflow enables to move risks" in several statuses as shown in the following picture.
The following table explains the meaning of each status:
| Status | Description |
|---|---|
| Default | A temporary status when the risk is initially created before the first save. |
| Draft | A risk in this status is draft and is not confirmed nor actioned yet. |
| Potential | A risk in this status is confirmed and shall be actioned. |
| Mitigated | In this status, the risk has been actioned and mitigated. |
| Cancelled | Risk cancelled. This is an end of life status. |
| Closed | In this status, risk has been threated successfully and no more actions are needed. This is an end of life status, meaning no further status transitions are allowed. |
Information
Risks records are organized in four sections:
- Identification, where identification data of the risk are recorded,
- Ownership & Organization, containing the assignment of the key roles enabled to manage the risk;
- Pre-mitigation Assessment, with the assessment details of the risk before mitigation actions;
- Post-mitigation Assessment, with the details of the risk after mitigation actions.
Detailed information on the meaning and use of every field can be found by pointing the mouse on the (i) next to each field. This will activate a tooltip with a brief description of the field.
Additional information can be found in the secondary forms of the record: attachments, related items, messages and history. See How To for more information.
Privileges
Risks can be created by the users to whom the corresponding privilege is granted (see Users & Groups for more information on how to set this privilege).
The lifecycle of the risk is managed by the roles described in the table below. Groups are pre assigned to the roles according to the settings (see Settings for more information on how to set these defaults). Initial assignments can be modified according to privileges choosing among the enabled groups (see once again Settings for more information on how to enable groups).
| Role | Description |
|---|---|
| DPO Group | Members of the group assigned to this role have full privileges. They can:
|
| Data Controller Group | Members of the group assigned to this role have view (read) privileges. |
| Data Processor Group | Members of the group assigned to this role have view (read) privileges. |
| Risk Assessment Team | Members of this group have several privileges. They can manage the entire lifecycle, being enabled to:
|
| Audit Team | Members of the group assigned to this role have view (read) privileges. |
| Owner | This role can be assigned to a single user among members of the groups previously described. The Owner has several privileges:
|
Reports
The list of risks can be filtered and exported to excel format from the view Risks.
Related processes
Risks can be related to actions, audits, data breaches, issues / non conformities, privacy impact assessments and processing activities.